The risk of cyberattacks is a constant threat and it can happen to any online business. One of the most notorious examples related to card data breaches is Zappos, the eCommerce company owned by Amazon, where hackers managed to access the account and card details of 24 million customers.
At first glance, data breaches like this might seem singular events, but the harsh truth is many online businesses are not prepared to face potential attacks. In response to this, the Payment Card Industry has come up with a set of rules and requirements that establish a secure system for online businesses and customers.
When reading the requirements, you might find yourself overwhelmed by the volume of information and the number of steps needed to start processing and storing credit card information from your customers.
Continue reading so you can find out which are the 4 levels of compliance, the mandatory steps of becoming PCI DSS compliant, and ways you can reduce the complexity of this process.
What is the Payment Card Industry Data Security Standard (PCI DSS)?
PCI DSS was introduced by major credit card networks in September 2006, to create a robust security process when accepting online payments or dealing with any online financial transaction. The guidelines are constantly updated to align with new technologies from fin-tech and eCommerce. In order to ensure that cardholder and sensitive authentication data is safely processed, stored and transmitted, online merchants and service providers need to create a secure infrastructure that is aligned with the PCI DSS requirements.
The entire process is validated by submitting a Self-Assessment Questionnaire (SAQ), or via annual audits made by security assessors who file your Report of Compliance. The most important aspect is that absolutely every online business needs to either submit the SAQ questionnaires – which come on different levels, depending on the needs of your environment – or to audit their environment via certified security assessors, if your company is a large enterprise.
Here are the 4 levels of PCI compliance:
- Level 1: You process over 6 million card transactions per year. – SAQ-D Questionnaire and audits made by security assessors are mandatory
- Level 2: You process 1 to 6 million transactions per year – SAQ mandatory, signed by a QSA or a trained PCI SSC ISA employee
- Level 3: You are handling 20,000 to 1 million transactions per year – SAQ mandatory
- Level 4: You are handling fewer than 20,000 transactions per year – SAQ recommended, not mandatory.
More details on the different types of SAQS can be found on the Security Standards Council PCI DSS Quick Reference Guide.
What are the Steps of Becoming PCI DSS Compliant?
Build and Maintain a Secure Network and Systems
The first thing you must do is install and manage a firewall configuration to protect your customers’ credit card data. By doing this you can manage, identify and document the connection between credit card data and other networks, and block suspicious or untrustworthy networks. This also ensures that nobody has direct access to the environment where the card data is stored.
Hackers are very versatile when it comes to passwords because they use exploits that leverage outdated settings so they can easily gain access to your system. The second step in becoming PCI compliant is to make sure that all your settings are up to date and you disable unnecessary accounts before installing any new systems on your network.
According to PCI DSS guidelines, you need to develop configuration standards for all system components and address existing vulnerabilities. Besides that, you need to have a system managed by people who know how to use cryptography in place, to ensure that the data is encrypted and untouchable.
Protect Cardholder Data with Strong Access Control Measures
The PCI DSS guidelines recommend that you should never store credit card data unless it is necessary for your business. However, if you are running a subscription business, it is mandatory to store your customers’ data for renewal purposes. In this case, you should have a data retention policy document authorized by regulators in place that tells you for how long you can store sensitive data. Otherwise, the PCI recommends erasing unnecessary data at least quarterly. Lastly, it is mandatory to document and implement processes that help you store public and private keys used for encrypting data.
Maintain a Vulnerability Management Program and Track Networks
Online businesses and users are common targets for malware that exploits system vulnerabilities. You must always make sure that your security software is running smoothly and is updated. By enforcing a constant secure environment, your business can stay protected from attacks and possible fines.
The best way to keep vulnerabilities in check is by establishing a ranking system based on the level of threat―low, medium and high―so your team can prioritize, organize and solve them. In other cases, vulnerabilities can automatically be removed by installing security patches provided by the security software provider.
Another point to take into consideration is the need to implement a security-driven software development culture in your organization. When dealing with sensitive data, your developers must build the project from the start with security in mind. In fact, this is the first thing that they should take into consideration before coding begins.
When you are selling online, your web applications face a lot of threats. In order to be PCI compliant, your public-facing applications must be continuously assessed for vulnerabilities, either manually or by web firewalls that monitor your traffic and send status reports around the clock.
What can you do to reduce the complexity of PCI DSS compliance?
It all starts with your payment provider and the checkout experience. As a merchant selling products and services online, you need to control the ordering experience, while following the robust recommendations of the PCI DSS guidelines.
The checkout you are using is the most important component of your online business and, competition-wise, it can also be a huge differentiator. Your team doesn’t have to invest a lot of energy and time as you can choose between solutions available on the market that can help you reduce the complexity of PCI DSS compliance to a SAQ-A self-questionnaire level, regardless of the volume of transactions handled.
Here are the types of checkout you can use to stay compliant and provide a secure order experience to your customers.
1. Use a Checkout page with URL Redirect model
With this checkout model, your customers are redirected from your website to a different page that enables shoppers to finalize their purchase without spending too much time in the shopping cart.
In terms of compliance, the checkout flow is hosted by the payment provider or a third-party company, which should have the highest level of PCI Compliance (Level 1). The cardholder data is automatically collected by the checkout provider, so you don’t have to touch the customers’ card data.
Given that this checkout type is hosted by the payment provider, you merely fill in the annual SAQ-A self-questionnaire provided by assessors to make sure that your business meets the minimum-security requirements. Put differently, a lengthy compliance process is reduced to the formality of filling in a questionnaire. Checkout flows like this are perfect if you want to save time in developing your own solution, as they are customized and optimized out of the box to increase conversion and payment authorization rates.
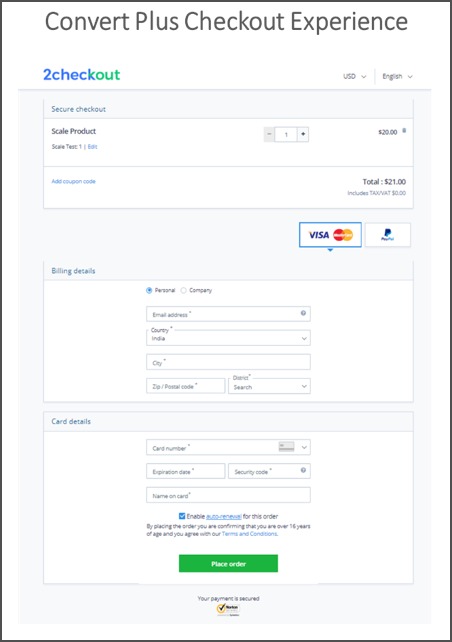
2. Use an Iframe Checkout
In terms of PCI compliance, the Iframe checkout is identical to the ones that have a URL Redirect model.
This checkout page is hosted by the payment provider, which means that you don’t have to worry about storing card data.
The main difference between an Iframe checkout and a traditional one is that the Iframe checkout offers your customers a unique experience. Your customers are not redirected to a different page and can place orders directly from your website. Thus, the buying process is sped up, so you can increase your checkout conversion rates.
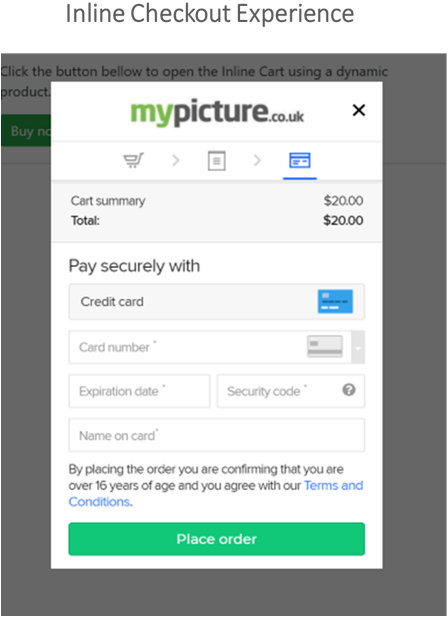
3. Implement a JS Ordering Form
In case you have an in-house checkout solution and your payment integration is made via an API, your PCI DSS assessment goes a level higher in comparison with businesses that use checkout pages hosted by a payment service provider. In this scenario, the best solution for you is to use a JavaScript form on top of your checkout one that collects, encrypts and transfers cardholder sensitive data directly to your payment service provider.
The first advantage of this solution is that you don’t have to worry about collecting sensitive data during the payment process, which drastically reduces the requirements of PCI DSS to the level of a SAQ A-EP self-questionnaire.
A second advantage is that you retain full control over the look and feel of your checkout flow.
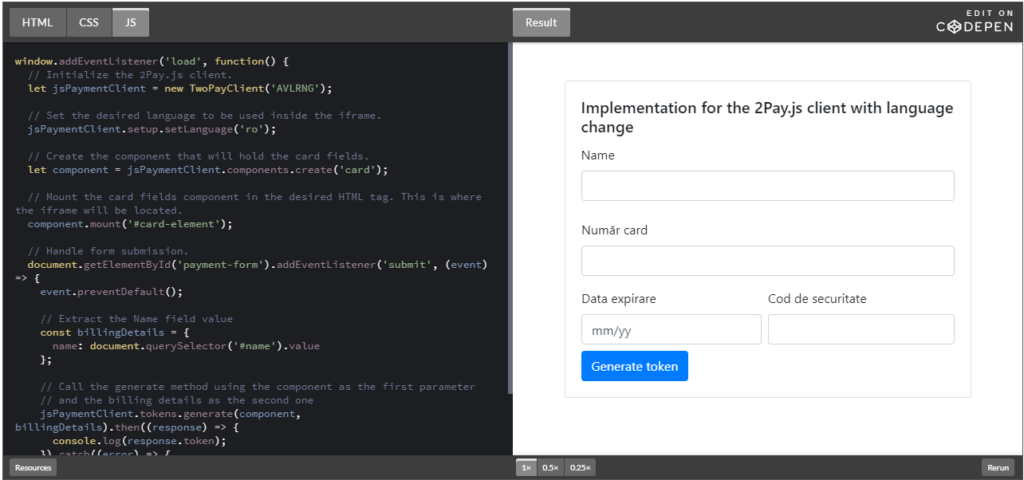
When it comes to implementation, it requires only a few lines of code and it allows your Payment Service Provider to intercept and tokenize (encrypt) sensitive credit card information, while storing it in their systems for a very short period, before it’s erased.
2Checkout’s newly launched 2Pay.JS payments solution incorporates all the advantages mentioned above and more, for the security and compliance of merchants who harness the power of APIs.
This brings multiple benefits to merchants who employ it for their eCommerce payment flows:
- Full-cart ownership while collecting payment details on your website
- Reduced complexity for compliance regardless of transaction volumes
- Easy to set up and integrate with just a few lines of code
- Extra layer of security for self-hosted checkout pages and compatible with multiple buyer flows (one-off and recurring payments, one-click purchases)
Conclusion
Whether you are a small, medium or large enterprise, the entire process of PCI auditing and validation can cost you a lot of money and time.
Using payment solutions like the ones provided by 2Checkout can drastically reduce your work and ensure that you are processing purchase transactions in a secure way. What’s more, a robust JS ordering form like 2Pay.js can considerably enhance the shopping experience on your website by helping build stronger connections to your customers. Opt for compliance and security features that do away with unnecessary complexity but bring new revenue increase capabilities to the table.
For further details on our 2Pay.js release, read our Knowledge Center article or check out our Implementation Guide.
Contact us at supportplus@2checkout.com to help you integrate 2Pay ordering for your eCommerce business.




