Every day, companies of all sizes are phished. Phishing attacks are becoming more sophisticated and harder to spot, making them a serious threat to businesses.
In the US, phishing attacks have cost businesses over $54 million, with over 241,342 affected in 2020.
So what is phishing? What are the most common types of phishing attacks? And most importantly, how can you protect your business from them?
This article will answer all those questions and offer tips to protect your business from phishing attacks.
Key Highlights
- Phishing is a cyber attack that uses fraudulent emails or websites to steal sensitive information such as login credentials or credit card information.
- Some of the most common phishing attacks are spoofed email, spear phishing, smishing, vishing and pharming.
- There are several steps businesses can take to protect themselves from phishing attacks, including implementing anti-phishing software and training employees on how to spot phishing emails.
- Phishing attacks are becoming more sophisticated, so staying up-to-date on the latest trends and methods is important.
What is Phishing?
Simply put, phishing is a cyber attack that uses fraudulent emails or websites to steal sensitive information such as login credentials or credit card information. Phishers can also use this information to access corporate networks and systems.
But it’s more than just some random person sending out emails. Phishing is a well-planned attack by cybercriminals who have studied their target. They know what to say and how to say it to trick you into giving them the information they want.
In some cases, the phisher will send out an email or create a website that looks legitimate. But when you click on a link or enter your information, it goes to the phisher instead of the actual website.
Phishing attacks are becoming more sophisticated and harder to spot. A recent study found that nearly 97% of people could not spot a phishing email. This is because attackers use increasingly sophisticated methods to make their emails and websites legitimate.
There are other reasons for the widespread attack.
For one, phishing attacks are relatively easy to carry out. All you need is an email account and basic knowledge of creating a website.
Another reason is that they’re effective. An IBM study reveals over 40% of cyber attacks started with phishing emails.
Lastly, phishing attacks are affordable. Cybercriminals don’t need to spend much money to carry out a successful phishing attack. Many tools and software required to carry out an attack are free.
Common Types of Phishing Attacks
There’s no shortage of ways cybercriminals can try phishing your sensitive information. Here are some of the most common types of phishing attacks:
1. Spoofed Emails
In this attack, you’ll receive an email that appears to be from a legitimate source, such as a financial institution or well-known company. The email will often include branding that looks legitimate and may even use the same logo as the actual company.
Here’s a phishing attempt we’ve been made aware of:
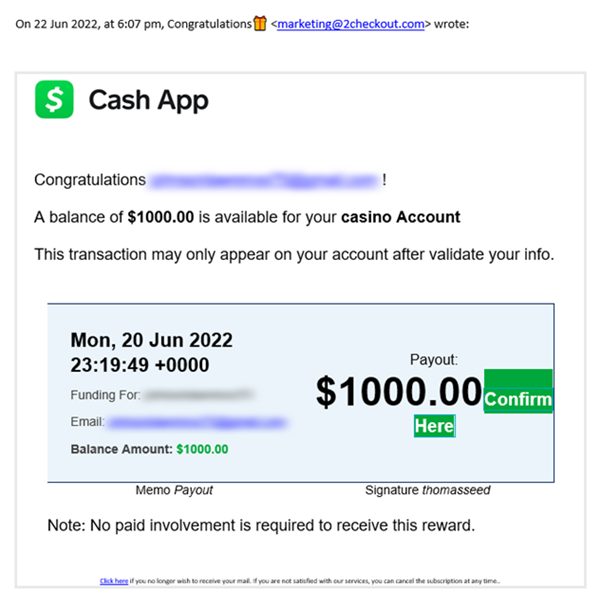
However, the email will usually contain typos or other red flags that should tip you off that it’s not legitimate. The email aims to get you to click on a link or attachment that will install malware on your computer or take you to a fake website where you’ll be asked to enter sensitive information.
An excellent way to spot a spoofed email is to hover over any links in the email before clicking on them. If the link destination doesn’t match the displayed text, it’s likely a spoofed email. If it also has random letters before or after the .com, .org, .net, etc., red flag. Also, check for spelling mistakes in the email or URL.
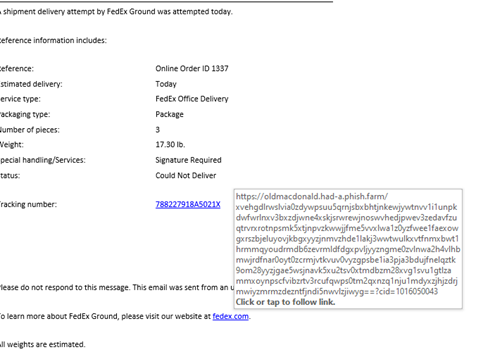
2. Spear phishing
This type of attack is similar to a spoofed email but targeted at a specific individual or organization. The attacker will usually research their target through information publicly available on the internet such as various social media networks, to gather information to make the email seem more legitimate.
For example, an attacker might send a spear phishing email to someone in a company that appears to be from the CEO. The email might contain information only the CEO would know, such as upcoming projects or plans. The goal is to get the recipient to take action, such as clicking on a link or attachment that will install malware or take them to a fake website.
3. Smishing
Smishing is a phishing attack that uses text messages instead of email to try and trick you into giving away their personal information. Smishing attacks are becoming more common as scammers have found that they can reach a wider audience with text messages than with email.
Smishing attacks usually come in the form of a text message that appears to be from a legitimate source, such as a bank or a government agency. The text message will often trick the recipient into clicking on a fake website link where they will be asked for personal information, such as their bank account number or Social Security number.
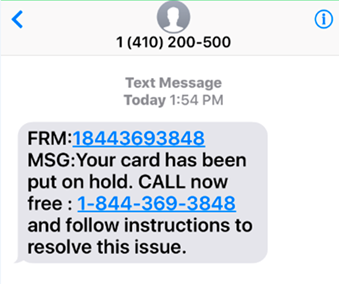
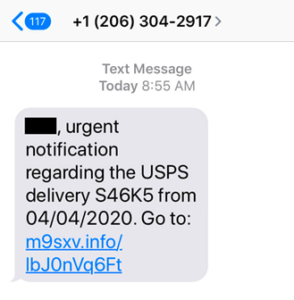
Smishing attacks can be difficult to spot because the text message may look like it is coming from a legitimate source. However, there are some things that you can look for to help you spot a smishing attack:
- The message is unsolicited and comes from an unknown number.
- The message is urgent or contains a sense of urgency.
- The message asks you to click on a link.
- The message asks you to enter personal information.
If you receive a text message that you think may be a smishing attack, do not click on any links or enter personal information. Instead, delete the message and report it to your cell phone carrier.
4. Vishing
Instead of text messages, vishing attacks use voice messages or phone calls to try and trick people into giving away their personal information.
The attacker usually poses as a legitimate organization, such as a bank or credit card company. They’ll often use automated call systems to make it seem like they’re calling from a real company.
The attack aims to get the person on the other end of the line to give up sensitive information, such as a credit card number or bank account login. They may also try to get you to install malware on your computer by telling you that you need to download a program to access your account.
Vishing attacks can be difficult to spot because the message may sound like it is coming from a legitimate source. However, there are some things that you can look for to help you spot a vishing attack:
- The call is unsolicited and comes from an unknown number.
- The caller is asking for personal information. The caller ID is spoofed to make it look like the call is coming from a legitimate source.
If you receive a phone call or voicemail message that you think is a vishing attack, do not call the number back or enter any personal information. Instead, hang up and report the incident to the Federal Trade Commission (FTC). You should also report the incident to your phone carrier.
5. Pharming
Pharming uses malware to redirect victims to a fake website without their knowledge.
Phishing attacks usually rely on social engineering to trick victims into clicking on a link that takes them to a phony website. Pharming attacks, on the other hand, do not require interaction from the victim – the redirect to the fake website happens automatically.
Pharming attacks can be difficult to spot because the fake website looks identical to the legitimate website. However, there are some things that you can look for to help you spot a pharming attack:
- The URL of the website is slightly different from the legitimate website. For example, the URL may use a different domain name or have an extra character in the URL.
- The website looks identical to the legitimate website but has a different URL.
How to protect your online business from Phishing Attacks
There are several steps you can take to protect your online business from phishing attacks:

1. Educate your employees about phishing
Employees should be aware of what phishing is and how to spot it. Employees should also know not to click on links or download attachments from unknown senders.
2. Use a secure email gateway
A secure email gateway can protect your business from phishing emails by filtering out malicious emails before they reach your employees.
3. Implement two-factor authentication
Two-factor authentication adds an extra layer of security by requiring a second factor, such as a code from a mobile app and a password.
4. Keep your software up to date
Attackers can exploit out-of-date software. Be sure to keep all your software, including your operating system and web browser, up to date.
5. Use a firewall
A firewall can help protect your network from attacks by blocking malicious traffic.
6. Back up your data
If a phishing attack targets your business, it’s important to have data backups so you can quickly recover.
7. Monitor your logs
Monitoring your logs can help you detect suspicious activity and investigate any potential attacks.
8. Report phishing emails
If you receive a phishing email, report it to the appropriate authorities so they can take action to protect other businesses from being targeted.
Conclusion
Phishing is a serious threat to businesses of all sizes. You can help protect your business from phishing attacks by educating your employees and securing your data. By staying vigilant in the face of fraud and adopting a holistic approach to cybercrime, you can better manage business risks.





