In an era defined by digital transactions, the global flow of payment data has become the lifeblood of commerce. However, this borderless economy operates on a foundation of distinctly bordered laws. For businesses leveraging the power of the cloud, this creates a critical challenge: how to innovate and scale globally while adhering to a complex web of local regulations governing data. This is the realm of data sovereignty and payment compliance, where the agility of cloud computing meets the demands of national and regional laws.
Who’s this article for
This article is meant for technology leaders, compliance officers, and business decision-makers in organizations that handle payment data. Whether you are a fintech startup or an established commerce business accepting payments online, in-store or via bank and ACH transfers, this guide will walk you through the core concepts of data sovereignty, the global regulatory environment, and actionable strategies for architecting a compliant payment processing framework in the cloud.
As businesses increasingly rely on cloud services for payment processing, understanding these regulatory requirements is not optional—it’s essential for survival and growth.
Understanding the core concepts and the converging challenges
To build a compliant strategy, a firm grasp of the foundational terminology is crucial. These concepts, while related, have distinct meanings and implications for your data governance and cloud architecture.
What is data sovereignty
Data sovereignty dictates that data is subject to the laws of the country where it is generated and collected, regardless of where it is physically stored and processed. Related to this, data residency is about the physical location of where data is stored and processed. A considerable number of regulations mandate data residency compliance as a baseline for meeting sovereignty requirements.
Data residency vs. data localization: key distinctions
Although these terms are sometimes used interchangeably, they have different meanings. Data localization is a legal requirement that mandates data be stored within a specific country’s borders. Data residency is a choice of strategy (the geographical location where an organization chooses to store its data); data localization is a legal obligation that enforces that choice.
If your customer data is generated in Belgium, France, or the Netherlands and stored in a German data center, it is subject to the data protection laws of each country, particularly the General Data Protection Regulation (GDPR). This concept extends beyond storage to include processing and accessing data, which has significant implications for how global companies manage their cloud infrastructure.

What does payment compliance entail
With organizations facing a barrage of attacks—79% of U.S. companies reported being victims of payments fraud in 2024—robust compliance is the first line of defense in maintaining the integrity of the payment ecosystem.
This critical area is subject to strict rules, like the prominent Payment Card Industry Data Security Standard (PCI DSS), a global standard outlining technical and operational requirements for securing cardholder data.
PCI DSS is a foundational pillar for payments compliance. Its requirements—including building a secure network, protecting stored cardholder data, and implementing strong access control measures—are non-negotiable for any entity that processes payments.
There are 4 levels of compliance in PCI, based on the number of transactions performed and every company processing payments should be aware of these.
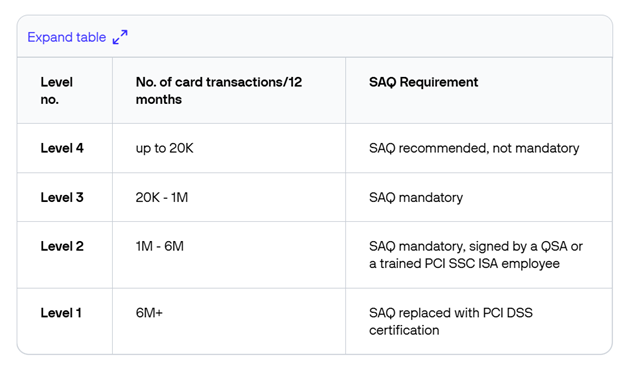
Source: Verifone Cloud
For the lowest level of compliance – level 4 – organizations are mainly faced with meeting the PCI requirements of their bank or payments provider. While they do have some specific obligations to perform, the good news is that they can considerably reduce the complexity of their PCI-DSS compliance.
Streamline your compliance efforts by working with payments provider 2Checkout. All of our software and hardware solutions are PCI-compliant. This simplifies your efforts to comply with financial and privacy regulations in new markets and channels
Another important standard shaping global payment interoperability is ISO 20022, which defines a universal data format for financial messaging. By promoting richer, structured data and standardizing communication between banks and payment systems, ISO 20022 enhances transparency, compliance, and efficiency across borders. Merchants can use this structured data for better analytics and insights into their payment data.
Other regulation examples include: EU’s open banking regulation PSD2 (soon to be PSD3), which regulates electronic payment services and protects sensitive financial information. A critical component of PSD2 is SCA (Strong Customer Authentication), which aims to bolster the security of online transactions. Similarly, 1033 in the US forces banks to allow third-party-provider access to bank account data.
Payment-specific regulations, such as the EU Instant Payment Regulation, are impacting banks and payment companies, while Know Your Customer (KYC), Anti-Money Laundering (AML) and sanction screening regulations are in widely place to prevent financial crime.
As global payment systems evolve, compliance must adapt to an increasingly diverse and fragmented ecosystem. Merchants today operate across multiple payment rails—from card networks to mobile wallets and instant payment infrastructures—each governed by its own security and data rules. At the same time, local payment methods continue to dominate consumer preferences in many markets, requiring merchants to meet domestic compliance standards alongside global ones. The need for robust, standardized, and secure compliance practices has never been greater—ensuring that speed, convenience, and trust advance together.
The implications of privacy and data protection laws
This type of legislation is mandating what data (including personal data) can be collected, where and how this data must be stored and processed, as well as how it can be accessed.
The GDPR in the European Union is the benchmark for comprehensive data protection regulation, but it’s far from the only one. Countries worldwide have enacted their own data protection laws, such as the CCPA in the US (more specifically, California), Brazil’s LGPD, India’s DPDP Act, and China’s PIPL. Each has similar as well as unique requirements for data handling, consent, and cross-border data transfers, forcing companies to adopt localized compliance strategies.
Understanding local cloud regulations
Cloud technology has become a cornerstone of modern payment operations, giving merchants the scalability, flexibility, and efficiency to innovate faster and reduce dependence on costly on-premises infrastructure. It enables rapid deployment of new services, easier integration with third-party tools, and improved resilience through stronger disaster recovery and business continuity capabilities. Merchants can choose from various cloud configurations—private, public, or hybrid—to align performance, security, and compliance needs with business goals.
Cloud regulations refer to specific laws enacted by governments or industry-specific regulations that focus on data security, data privacy and compliance, mandating how data, particularly sensitive personal or financial information, is handled in the cloud. Examples include the key regulations mentioned above, as well as strict security standards that cloud providers need to adhere to.
Local cloud regulations vary by region and by country, but all focus on data residency, privacy and security. Strict data localization requirements are often included in data protection laws, which are the key frameworks here. As these laws usually require data to be stored on servers physically located within the country or region, their requirements directly impact the choice of cloud providers and the configuration of cloud services.
Cloud compliance refers to the process of adhering to all of these regulatory standards, international laws and mandates, and industry best practices (frameworks, benchmarks) in the context of cloud computing. The goal is to ensure that the way data is stored, managed and protected in the cloud meets these general or industry-specific regulatory requirements.
In recent years, due to concerns over data sovereignty, the concept of the sovereign cloud has gained significant traction—especially in Europe. A sovereign cloud ensures that data, operations, and support remain entirely within the borders and jurisdiction of a specific country or region. This approach provides an additional layer of assurance for organizations managing highly regulated data, such as payment or personal information, or for those subject to national restrictions on cross-border data transfers. Beyond compliance, sovereign clouds also address growing concerns about data control, national security, and geopolitical risk, offering organizations greater transparency and trust in their digital infrastructure.
When assessing providers, prioritize those with regional data centers that meet not only all the needed technical aspects, but also residency laws. This is a foundational step in building a compliant payment architecture. All major cloud providers—such as AWS, Azure, and Google Cloud—allow customers to specify data regions.
The stakes: Risks of non-compliance
It’s clear just by looking at these definitions and concepts that businesses today face a several-pronged challenge. Mismanaging this convergence isn’t just a technical misstep; it’s a significant business risk. Failure to meet data sovereignty and payment compliance standards carries significant risks:
- Financial penalties: The EU alone imposed over €1.2 billion in GDPR fines in 2024.
- Data breach costs: The average global cost of a data breach reached USD 4.44 million in 2025, including legal fees, remediation, and operational downtime.
- Reputational damage: Loss of trust can have long-term consequences that directly impact customer retention and market position.
As organizations increasingly depend on the cloud for payment processing, compliance is not just a legal requirement—it’s essential for business continuity and growth.

Mastering payment compliance in a cloud environment
Achieving payment compliance within the constraints of data sovereignty requires a dedicated and multi-faceted approach, starting with foundational security standards.
Map and classify your payment data
Effective data governance begins with knowing what data you have to deal with. Identify what payment data you process, where it resides, and how sensitive it is. Classify data types according to their regulatory requirements and associated risk levels (e.g., cardholder data, personally identifiable information).
Data mapping clarifies cross-border data flows and supports compliance decisions such as encryption, localization, and access control—ensuring sensitive data is protected according to both PCI DSS and local data protection laws.
Manage cross-border data transfers
In the payments and fintech ecosystem, cross-border data transfers are vital for payment processing, fraud detection, and analytics—but they’re heavily regulated. Under GDPR and the Schrems II ruling, personal or financial data can only be transferred outside the EEA if equivalent protections are guaranteed. This typically involves mechanisms such as:
- Adequacy decisions
- Standard Contractual Clauses (SCCs)
- Binding Corporate Rules (BCRs)
For fintechs and merchants using multi-cloud or API-driven infrastructures, this means performing Transfer Impact Assessments (TIAs) and enforcing strong technical measures like encryption and pseudonymization. SCCs remain the most widely used mechanism, but they require operational safeguards and legal due diligence.
In addition, laws like the US CLOUD Act (Clarifying Lawful Overseas Use of Data Act) add another layer of complexity. This act allows U.S. federal law enforcement to compel U.S.-based technology companies to provide requested data, regardless of where that data is stored globally. This creates a potential conflict with data privacy laws like the GDPR, making the choice of cloud provider and their corporate nationality a critical factor in data sovereignty planning. This concern is a major driver behind the sovereign cloud movement, with 84% of European organizations now using or planning to use sovereign cloud solutions.
The ultimate goal is to build privacy-resilient architectures—where compliance, transparency, and trust are embedded into every layer of data processing.
Key security and compliance standards to check for
When choosing a cloud provider, look for certifications that demonstrate a serious commitment to security and compliance:
- ISO 27001/ ISO 27000: An international standard for information security management systems, providing a framework for managing risks and protecting data.
- SOC 2 (System and Organization Controls): An auditing standard that ensures service providers securely manage data to protect organizational and client interests.
- NIST (National Institute of Standards and Technology): The U.S. National Institute of Standards and Technology provides cybersecurity risk management frameworks. Integrating the NIST Cybersecurity Framework (CSF) with the MITRE ATT&CK model improves an organization’s capacity to predict, identify, and react to threats.
- CIS (Critical Security Controls): A set of prioritized, actionable best practices to guard against the most common cyber-attack vectors.
Some regions also impose specific cloud security frameworks. For example, the U.S. FedRAMP standardizes security assessments and authorizations for federal cloud services.
Achieving cloud compliance means implementing strong security controls, performing regular audits, and continuously monitoring for vulnerabilities and misconfigurations.
Another important factor is provider accountability, necessitating the execution of data processing agreements (DPAs). These agreements ensure that the provider’s compliance is a binding contractual obligation.
Developing a strategic framework for payment data sovereignty
To navigate the intersection of data sovereignty, payment compliance, and cloud operations, organizations should adopt an integrated framework built on governance, secure architecture, and robust controls—mapping data flows, designing compliant infrastructure, enforcing encryption and access policies, and maintaining a tested incident response plan to ensure resilience and trust.
Building on this foundation, cloud-native architectures can further strengthen compliance and scalability, allowing organizations to design systems that are inherently adaptable, resilient, and aligned with evolving regulatory demands. Because payment and data protection compliance is about more than just avoiding risk. It’s also about enabling secure, scalable growth and staying competitive in an increasingly complex payments landscape.

FAQs
1. What is recommended — hybrid, on-premise, or multi-cloud — for managing payment compliance and data sovereignty?
A hybrid or multi-cloud strategy is often best. It allows sensitive or regulated data to remain in-country — whether in an on-premise, private, or sovereign cloud environment — while leveraging global cloud capabilities for scalability and innovation. This balance supports both performance and compliance, provided you clearly define where data is processed and implement strong encryption and access controls.
2. Are there potential conflicting laws related to data protection?
Yes. Conflicts often arise between regional privacy laws (like the EU’s GDPR) and extraterritorial acts (like the U.S. CLOUD Act). For example, a U.S.-based provider could be compelled to hand over data stored in the EU, creating tension with European privacy rules. The solution is to use contractual, legal, and technical safeguards—such as Standard Contractual Clauses (SCCs) and encryption with EU-based key management.
3. If we outsource payment compliance to a provider and there’s a breach, who is responsible?
Responsibility is shared. The provider is accountable for maintaining PCI DSS compliance and infrastructure-level security, but your organization remains responsible for ensuring that provider compliance is verified and that data is used lawfully. This should be clearly defined in your Data Processing Agreement (DPA) and incident response plan.
4. What recommendations do you have to mitigate data fragmentation across systems?
Start with data mapping and classification—knowing where each data set lives, what laws apply, and who can access it. Implement centralized data governance policies and use interoperability frameworks. Consider tools for unified monitoring and enforce data minimization principles to reduce unnecessary replication.
5. How can we future-proof our compliance architecture as regulations evolve?
Adopt compliance by design principles—embedding data protection and sovereignty requirements into your architecture from the start. Maintain continuous monitoring, automated audit logs, and adaptable policies that can align with new frameworks (e.g., PSD3 or evolving AI-related privacy rules). Periodic third-party audits are also key to maintaining readiness.
6. How often should compliance and data governance frameworks be reviewed?
At least annually, or whenever you expand to a new market, adopt a new cloud provider, or undergo major system changes. Regulations evolve quickly—reviewing your risk assessments, data maps, and provider agreements ensures ongoing alignment with current laws and standards.




